Real-world cyberattacks have caused drastic damages to critical infrastructures such as power systems, water treatment plants, and manufacturing sectors. To prevent our society from catastrophic disruption, it is critical to rapidly and accurately detect, localize, and recover from security incidents.
Our research develops automated tools to identify deep vulnerabilities in critical infrastructure systems, capture stealthy attacks across digital and physical domains, and implement the defense-in-depth strategy in the systems. Our interdisciplinary work uniquely combines rigorous software testing theory, robust attack provenance techniques, high-fidelity physical modeling and advanced machine learning algorithms to enable a semantics and context-aware approach to the security of critical infrastructures.
We develop innovative solutions to enhance the cybersecurity of critical infrastructure through proactive defense, detection, localization and mitigation approaches:
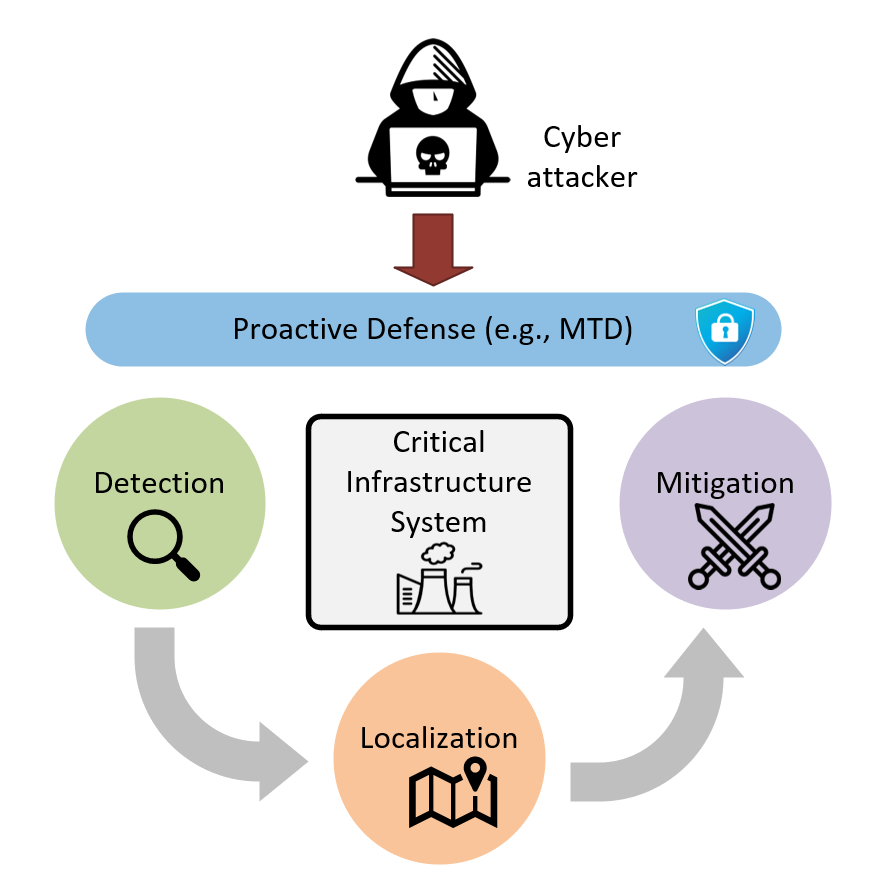
- Proactive Defense: It is the first layer of security and it encompass the techniques that increase the difficulty for adversaries to launch successful attacks. It includes conventional cybersecurity best-practices (e.g., access control, firewall) as well as sophisticated strategies such as moving target defense, where controlled dynamic changes are introduced to increase uncertainty and complexity for attackers.
- Detection: Consists on determining the presence of an attack in the system. Particularly, we have developed physics-based attack detection strategies that leverage the unique physical properties of power and energy systems along with machine learning and AI to identify changes that are not consistent to nominal system behavior.
- Localization: After detecting an attack, it is necessary to identify the location of the compromised device in order to execute the adequate corrective actions. This requires to understand the unique interdependencies between cyber and physical components.
- Mitigation and Recovery: Consists on automatically controlling non-compromised devices and energy assets in order to decrease the impact caused by an attack and maintain the operation of the system. Mitigation and recovery integrate the operation of physical energy devices (e.g., energy storage) and cyber components that are isolated, patched, or reconfigured.
